How to Cashout all CCs to BTC
How to Cashout all CCs to BTC How to Cashout CCs to BTC INTRODUCTION Everything I have written here is from personal experience, I have tried my best to explain…

How to Cashout all CCs to BTC How to Cashout CCs to BTC INTRODUCTION Everything I have written here is from personal experience, I have tried my best to explain…

HOW TO SKIM CREDIT CARD INFORMATION. CREDIT CARD SKIMMING TUTORIAL SKIM CREDIT CARD INFORMATION What do you need to begin as an expert (!), And as profitably as conceivable as…

How to cashout dumps? Professional guide for dumps cashout! Instructions on How to Cashout Credit Card Dumps – It applies generally to the US, yet others can get a…

How to create your BIN list - Updated Guide How to create your BIN list: Step-by-step instructions to make your BIN list – Developing and improving your BIN rundown will…

Best Proxy servers Recommended for Users Best Proxy servers Recommended Proxy servers take into account you to arrange your program to course your program traffic through that machine, which at…

ANTIDETECT BROWSER ( 100% YOUR CARDING SUCCESSFUL ) Antidetective browser. Consideration! The product isn't on the worker's side. Contenders programming projects can record every one of your activities on the…

How to Hack Android Devices Using Metasploit How to Hack Android Devices In this tutorial, I'll be teaching you how to hack Android devices such as phones and tablets using…
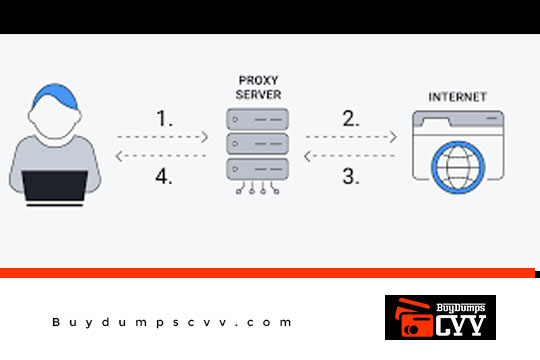
DIFFERENCES BETWEEN VPN, SOCKS5, SSH, AND TOR DIFFERENCES BETWEEN VPN, SOCKS5, SSH, VPN On the off chance that you are occupied with virtual checking or plan to begin, you ought…

Anonymous Surfing to Protect Your Privacy Anonymous Surfing HOLA VPN Hola is a peer-to-peer network that provides everyone on the planet with the freedom to access all of the Web!…

Private security Tutorial for newbies/Amateur Private security Tutorial Check Windows Update and Office Update regularly (_http://office.microsoft.com/productupdates); have your Office CD ready. Windows Me and XP users can configure automatic updates.…
You cannot copy content of this page